
17 min read
Source Code NDA: Everything You Need to Know
In our previous article about a Non-disclosure agreement (NDA), we discussed the process of protecting intellectual property in app development using NDAs. And source code NDA is our today’s focus, as long as it is one of the key components of the software you should protect.
The source code is the basis of any software system. Once you’ve transformed your code into object code, you can’t easily convert it back. Hackers can do reverse engineering (this article tells a lot about what reverse engineering is) but the result will highly likely not be the original source code.
When someone wants to hack a software system, access to its original source code is the first thing the hacker should think about. That’s why it’s highly important to employ efficient measures in order to protect your source code. As a unique intellectual property created by humans, the source code can be considered confidential information and subject to an NDA (a definition of confidential information can be found here).
In this article, we’ve covered:
- Risks associated with source code
- How to make your source code NDA relevant for protecting it
- Non-legal ways for protecting your code
- Other ways to hack a program
- And a template for your NDA.
NDA for Source Code: Definition and Types
Source code represents a sequence of commands or statements written in a human-readable form. This sequence tells the computer what to do to execute the program. Programmers usually write it in one of the high-level programming languages (e.g. Python, Java, C, C++, etc.)
To be executed by the computer, the source code is converted into low-level object code (binary machine code or bytecode). Object code in turn is non-readable for humans.
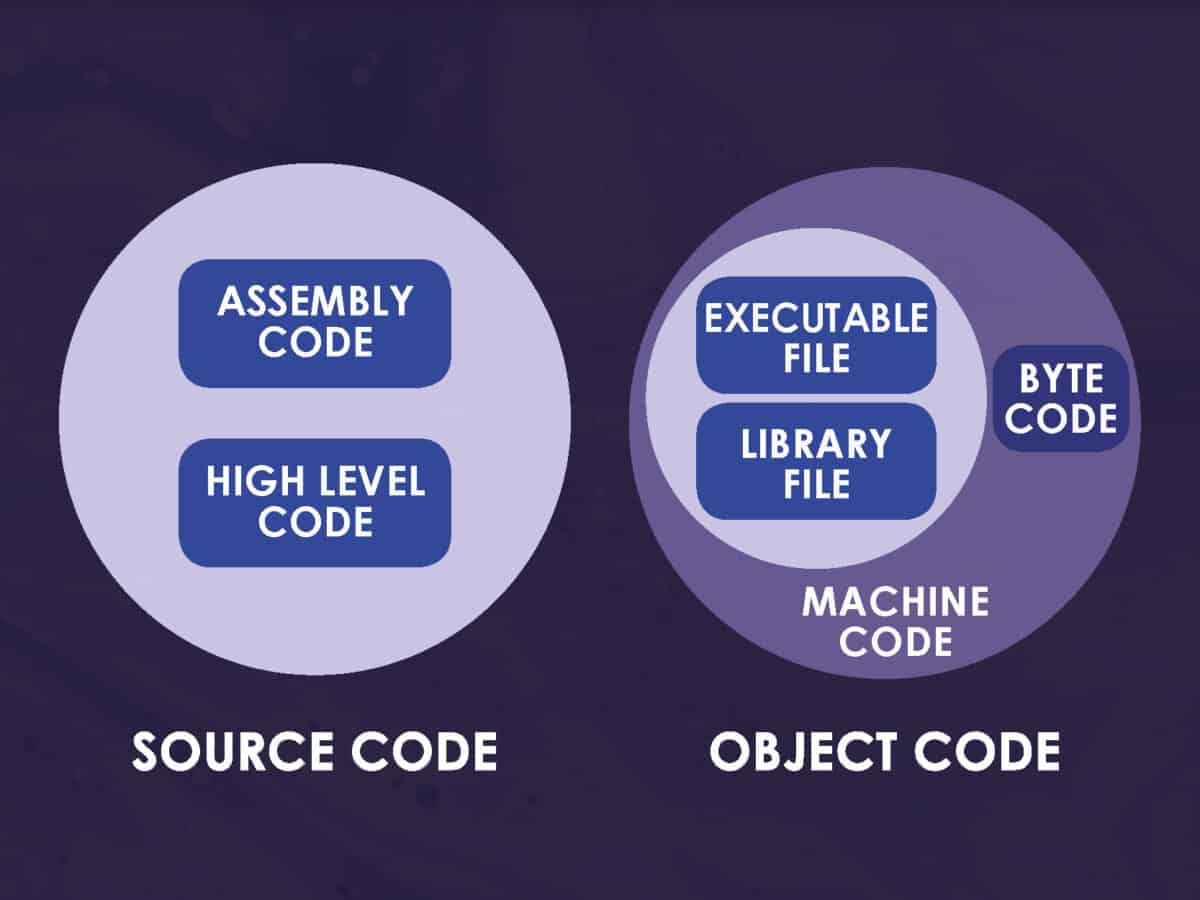
Proprietary and Open Source Code
So, let’s first determine two different source codes: a proprietary source code and an open-source one. The first one is definitely a trade secret you should protect. Once the second one is a community child and cannot belong to a single person.
| Software source codes→Factor ↓ | Proprietary | Open-source |
| Developers and maintainers | — developed by a company or external contractors like an outsourcing company — belongs to an individual or a company | — developed and maintained by a community |
| Public access availability | — not publicly available to access and change | — published and legally available to end-users so that anyone can access, change, and use it |
| Changes and redistribution availability | — can be considered intellectual property and therefore confidential information to be legally protected by intellectual property rights(with copyright or an agreement like NDA). For example, when you install Apple or Microsoft products, you have access only to their compiled executables | — can be edited and redistributed, i.e. anyone can take it and build their own program on top of it. For example, Linux OS code is open meaning that anyone can run, analyze, change, spread, or even sell copies of that modified code under the same license |
Reasons for Protecting Your Source Code from Disclosure
So what are the possible security threats you can address using source code NDA to protect your code? Here are the most notable of them:
- Copying. Your code often contains implementations of various custom ideas for your software. And you surely don’t want to share them.
- Using by competitors in any possible way. This means not only copy-pasting it into their products, with or without editing. They can analyze your code and then implement your successful solutions.
- Public exposure. If the code of your product becomes publicly available, it gets so much easier for hackers to explore it and identify existing flaws.
- Errors like buffer overflows and memory leaks. Hackers often use these widely-known types of vulnerabilities to get control of the program execution in order to damage files, expose private information, access other related systems, etc.
- Possible backdoors. Each dishonest software developer can intentionally leave security holes (backdoors) in the website, mobile app, or any other system they develop. Such people then quit their software development company and use these backdoors for criminal purposes.
- Failed due diligence. Before investing in a software project, VCs and business angels always pay maximum attention to the level of security of the related intellectual property. And if they consider your protection measures insufficient, you will likely fail to receive funding.
The Bangladesh Bank $1bln Heist Attempt
Indeed, each cybercrime is unique and may or not include access to the source code. Sometimes, a single known vulnerability of a third-party component is enough to open a way into the system. Even a single extra leverage opens up tremendous possibilities, or a silly mistake can ruin seemingly ideal cybercrime.
The Bangladesh Bank Heist story perfectly illustrates the statement above. In February 2016, a group of hackers called Lazarus Group, affiliated with the DPRK government, committed a massive theft from the state-owned Bangladesh Bank.
Hackers used a customized version of the Dridex malware to pass through a bank cybersecurity system. In January 2015, several bank employees received an email from a candidate with a CV link attached, and one of the employees then downloaded it.
Suddenly, the malware penetrated the corporate network and reached the SWIFT processing module. Then, it just had to wait until the special moment. And the hackers chose the moment ideally.
Fraudulent transactions started sending on February 4 at 20:00, when the working day in the Bangladesh Bank ended. An attempt of clearing out the $1bln dollar account led FRB staff to send clarifying messages. But nothing happened in return. All of a sudden, a printer that was aimed at printing these incoming messages crashed a bit before. It was a part of the plan. too.
The next day was Friday — a holiday in Bangladesh. And when Sunday came — the next working day in Dhaka — it was a weekend in the FRB’s office in New York.
But hackers bought one more day using Filipino Rizal Commercial Banking Corporation (RCBC) bank account as a destination for transactions. Monday 8th of February was a local holiday here. So, Lazarus Group had about five days for making everything as planned.
However, the banking staff wired only 5 of 35 transactions totaled at $101mln. The destination of the remaining transactions was RCBC’s branch office at Jupiter Street in Manila. Luckily, the same Jupiter name had an Iranian ship under sanctions. This lucky chance led to halting the remaining 30.
A small spelling mistake in orders led to a reversal of $20mln. Later, authorities managed to return $16mln more. Another $31mln was paid to a mysterious Chinese Xu Weikang who then disappeared. The last $34mln was successfully laundered without a trace.
You can read the full story of the Bangladesh Bank Heist published on BBC.
How to Protect Your Source Code with NDA
Below are some important approaches to how you can protect your code with NDA.
Explicitly Include Source Code and Algorithms in NDA as Protected Entities
Add the source code to the range of the items that are defined as “confidential information” in your NDA.
Apart from the source code overall, this range should also include code components such as:
- Algorithms and methods;
- Ideas behind the code (descriptions of the features in any form);
- Software specifications or technologies, once developed specifically for your software;
- Diagrams, data flows, and other outputs of the code likewise any other sensitive information.
Add a Statement Directly Prohibiting the Disclosing Party Your Source Code Disclosure
Explicitly prohibit the recipient party from disclosing confidential Information (including the code) to any other party. The best option is to set an exception in a form of extra written permission.

Prohibit Further Usage of a Source Code Anywhere Outside Your Safe Environment
Clearly express that the receiving party is not allowed to use or reuse the code, its components, or pieces, outside the current project. If you’re going to involve a third party and give them access to the code, you should explicitly specify their rights and obligations related to the source code, as well.
Add to NDA Source Code Legal Storage Explicitly
Agree on specific storage (server, cloud storage, retrieval system, database, etc.) for your source code, and express it in the NDA. It also makes sense to determine the ways the receiving party can and cannot store the code.
Prohibit Any Transferring of Rights: Your Source Code Is Yours Forever
Add a clause stating that the receiving party is prohibited from sharing any rights with any other party.
Assigning an independent contractor (a freelancer), remember in either case, that, according to copyright law, the results of the intellectual work of a developer belong to them by default if not stated otherwise. That’s why you should add a clause stating that all the work produced by this vendor during the project is “work for hire”. As a result, all the proprietary rights for such results will come to the client company.
Force Other Parties To Return or Delete your Trade Secrets and Source Code After Finishing the Collaboration
State that the receiving party should immediately return and delete the confidential information and its copies from everywhere upon the project’s completion. The best practice is to add a full list of people and companies covered by this requirement.
Define the Jurisdiction and Governing Law That Should Be Applied in a Case of Violation
Add a clause specifying where and based on which regulations the disputes must be tried in a case of unauthorized disclosure. The governing and copyright laws can be from different areas and countries. In this case, it doesn’t matter where the selected court is.
Source Code NDA Template
There is no particular NDA for the code. However, you can use a generic NDA template and customize it to your special needs. Use this link to download it in PDF form.
But this is not the last valuable thing we’ve prepared for you. The last and probably the best one is a ready-made “Intellectual Property” clause we’ve usually used in our non-disclosure agreements.
This clause is well-crafted and has proven its flawlessness many times. So, you can safely grab this PDF file and copy-paste its text into your agreement template without edits.
EULA — a Non Disclosure Agreement Counterpart for Ready-Made Software
When selling copies of ready-made software products like computer programs, you cannot sign an NDA with every single buyer. And the End-User License Agreement (EULA) is here to help. Usually, the EULA includes a clause setting restrictions on reverse-engineering of the software, including any disassembling or decompiling procedures with the existing form of code.
This kind of agreement is out of the scope of the current article. You can find out more about EULA in this guide. You can also review this step-by-step EULA online generator.
How Else You Can Protect Your Source Code?
As you can see, NDA isn’t an ultimate protecting measure for your code. Let’s take a look at other efficient approaches to help avoid the previously mentioned security threats.
Code Obfuscation
Obfuscation of the code is an efficient way of preventing executable files from decompiling. This approach is aimed at making your code as hard to understand for the reader as possible, keeping it fully functional. Obfuscation tools act at different levels:
— changing names of the variables and functions to meaningless randomly generated markers (name obfuscation),
— modifying the logical structure of the code (control flow obfuscation),
— combining simple mathematical expressions into more complex (arithmetic obfuscation),
— changing the existing commands into unique virtual machine instructions (code virtualization),
— many other levels and techniques.
Strict Access Control
Implement a reliable role-based access control system and give access to reliable parties only. Make sure that your repository cannot be accessible any other way. Locating your server in a closed perimeter free of any outsiders can be an expensive yet highly efficient additional measure.
Using Private Cloud Storage
Storing the source code in the private cloud makes decompiling attempts nearly impossible due to a lack of access.
How FAANG Companies Protect Their Code

Don Pinkus, a former engineer of Meta (ex-Facebook), shared some insight on how FAANG-level companies protect their code:
“Pretty much nothing physically stops you from copying and pasting the code, and sending it to yourself. The legal and career repercussions for doing this would be severe.
Also, most of the code isn’t really that cool on its own. It’s not like you can just copy-paste FB’s code and have Facebook. You need all of the data that the algorithms use, infrastructure, and much more.
Some of the security measures are more locked down, and a lot of the employees never need to interact with them.
Also, you only code on FB’s codebase on your work computer. There’s pretty much no reason for the code to ever leave your work computer — so code doesn’t really just “leak” over time.”
Conclusion
Protecting your source code is an important practice to help avoid some serious security threats. When forming the project NDA, you should include the statements about source code as one of the incremental pieces of confidential information NDA will protect.
By the way, NDA isn’t a guarantee for your source code from being disclosed, re-used, or analyzed. You can find some other efficient protection measures above. Among them are code obfuscators, stricter access control, and private cloud storages.
Remote tech teams & the future of work blog
Remote tech teams & the future of work blog
Your form has been successfully submitted.

